This is a complete guide to the Vigenère cipher and the tools you need to solve it. Read about its unbreakable history and fun facts, and learn about cryptanalysis methods, or use the Vigenere tool to solve it automatically.
Are you unsure about the cipher type? Use the Cipher Identifier to find the right tool.
Vigenere Tool
Instructions
You can decode (decrypt) or encode (encrypt) your message with your key. If you don't have any key, you can try to auto solve (break) your cipher.
Settings
- Standard Mode v s Autokey Variant: The Autokey mode is a stronger variant of the cipher, where letters of the plaintext become part of the key. It eliminates the periodic repeats otherwise seen in polyalphabetic ciphers.
- Language: The language determines the letters and statistics used for decoding, encoding and auto solving.
- Min/Max Key Length: This is the search range for keys when auto solving a cipher.
- Iterations: The more iterations, the more time will be spent when auto solving a cipher.
- Max Results: This is the maximum number of results you will get from auto solving.
- Spacing Mode: This is about the spaces (word breaks) in the text. In most cases it should be set to Automatic. In case a specific letter (for instance X) is used as word separator, set it to Substitute.
Note: Auto Solve will try in the mode you select (Standard Mode or Autokey mode). Standard mode is the most common, but if you don't know the mode, you should try both.
Auto Solver options
Knowing the encryption key
Auto Solve results
| Score | Key | Text |
|---|
Still not seeing the correct result? Then try experimenting with the Auto Solve settings or use the Cipher Identifier Tool.
What is the Vigenère Cipher?
The Vigenère cipher is a polyalphabetic substitution cipher that is a natural evolution of the Caesar cipher. The Caesar cipher encrypts by shifting each letter in the plaintext up or down a certain number of places in the alphabet. If the message was right shifted by 4, each A would become E, and each S would become W.
In the Vigenere cipher, a message is encrypted using a secret key, as well as an encryption table (called a Vigenère square, Vigenère table, or tabula recta). The tabula recta typically contains the 26 letters of the Latin alphabet from A to Z along the top of each column, and repeated along the left side at the beginning of each row. Each row of the square has the 26 letters of the Latin alphabet, shifted one position to the right in a cyclic way as the rows progress downwards. Once B moves to the front, A moves down to the end. This continues for the entire square.
Also, other alphabets than the English alphabet can be used in a similar way to construct a tabula recta.
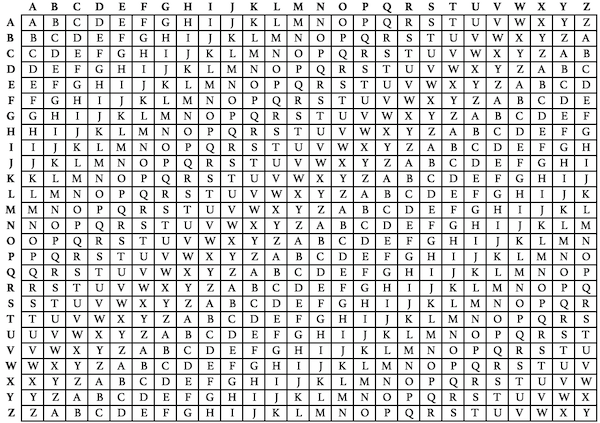
Let’s take this plaintext phrase as an example:
IMPROVE YOUR PUZZLE SOLVING SKILLS
After finalizing the plaintext, the person encrypting would then pick a secret key (a keyword), which would help encrypt and decrypt the message. Our example secret key here is:
BOXENTRIQ
The next step is repeating the secret key enough times so its length matches the plain text.
IMPROVE YOUR PUZZLE SOLVING SKILLS
BOXENTR IQBO XENTRI QBOXENT RIQBOX
Once the two lines are split into five-letter groups, start encrypting. Take one letter from the plaintext group and a letter from the secret key group (we’re going to start with I and B), and find the entry in the tabula recta where the row and column intersect. For this example, the first letter of the encrypted cipher text is J.
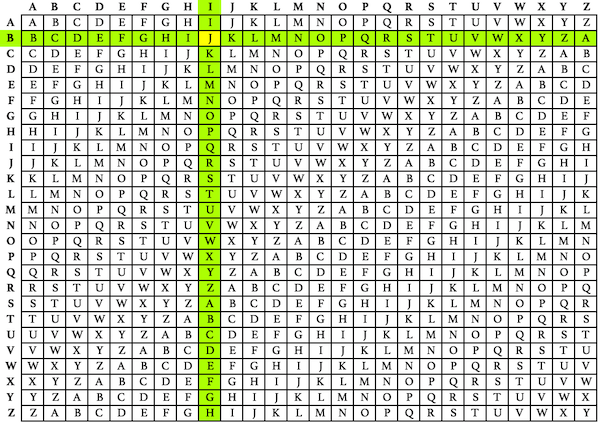
Once you’ve done that for every character, your final encrypted text should look like this:
JAMVB OVGEV FMYMS CMIPZ SMAZJ SYMZP
You can use this cipher for short or long messages. Once you’ve mastered the tabula recta, the encryption process is easy!
How to Decrypt it
If you have the secret key, decrypting is as easy as encrypting. You can work backwards using the tabula recta. First repeat the secret key so its length matches the cipher text.
JAMVB OVGEV FMYMS CMIPZ SMAZJ SYMZP
BOXEN TRIQB OXENT RIQBO XENTR IQBOX
Using the tabula recta, find the row that corresponds to the first letter in your secret key text- in our case, B. In the B row, find the corresponding cipher text letter J. The vertical column where that cipher text letter is located reveals the plaintext letter I.
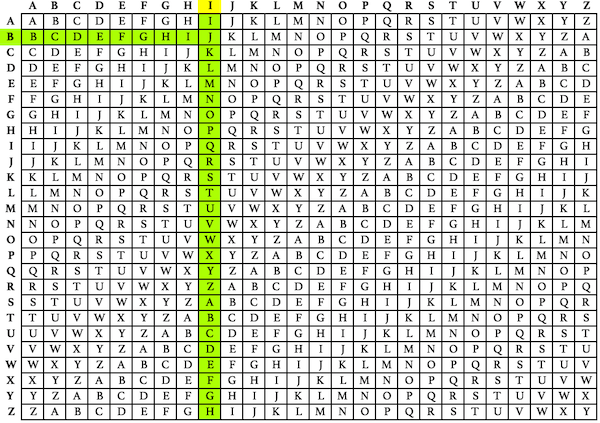
The Vigenère cipher can also be described and then decrypted algebraically, by assigning each letter from A to Z a value from 0 to 25, with addition being performed modulo 26.
How to Break It
Of course, these decryption methods only work if the secret key is known. In his initial attack against the Vigenère cipher, Friedrich Kasiski had success by examining repeated strings of characters in the cipher text, which could indicate the length of the key. This method is now called the Kasiski examination or Kasiski test. Finding more repeated strings of characters helps narrow down the length of the potential secret key. Once the length of the secret key is known, the cipher text is rewritten into a corresponding number of columns, with a column for each letter of the key. Each column is then made up of plaintext that’s been encrypted by one Caesar cipher. The code-breaker then breaks the cipher text in a similar way to a Caesar cipher.
Auguste Kerckhoffs improved on Kasiski’s method by matching each “column's letter frequencies to shifted plaintext frequencies to discover the key letter (Caesar shift) for that column.” Once the code-breaker knows each letter in the secret key, all they have to do is decrypt the cipher text using a Vigenère square.
Another option is the key elimination method. If you guess the key length and then subtract the ciphertext from itself, offset by the key length, it will eliminate the secret key. The result will be the plaintext subtracted from itself, offset by the key length. If any words longer than the key length can be guessed, their self-encryption can be searched for.
Related Ciphers
The creation of the Vigenère cipher in 1553 marked a major development in cryptography. It’s the best-known example of a polyalphabetic cipher, and its structure helped to innovate a new generation of more advanced polyalphabetic ciphers, like the Enigma machine.
Caesar Cipher
The Caesar cipher was named for Julius Caesar. It’s a simple substitution cipher where each letter of the plaintext phrase is replaced with a different letter from a fixed position up or down the alphabet. If a Caesar cipher has a right shift of four, A is replaced by E. If the cipher has a left shift of four, A becomes W. It prevents a regular layperson from reading your coded message, but once the code is broken, it’s extremely easy to figure out the plaintext. The Caesar cipher is equivalent to a Vigenère cipher with just a one-letter secret key. Julius Caesar used this cipher in his private war-time correspondence, always with a shift of three. Caesar’s nephew Augustus learned the code from his uncle, but encrypted his messages with a shift of only one, but without wrapping around the alphabet. Generally, this cipher is most effective when your enemies are illiterate (as most of Caesar’s opponents would have been).
Beaufort Cipher
The Beaufort cipher is another polyalphabetic substitution cipher that uses a tabula recta to encrypt and decrypt messages. The tabula recta used with the Beaufort cipher is called a Beaufort square, and is similar to a Vigenère square except it’s arranged in reverse order, with the letter Z coming first, and letters cascading in reverse alphabetical order from there. A message encrypted using the Beaufort cipher can be decrypted with a Vigenère square, as long as every letter is subsequently reversed (A turns into Z, B to Y, and so on). This cipher was created in the late 19th century by Sir Francis Beaufort, an Irish-born hydrographer who had a well-respected career in the Royal Navy.
Gronsfeld Cipher
The Gronsfeld cipher was likely created by a man named Jost Maximilian von Bronckhorst-Gronsfeld, a Bavarian field marshal. Despite his aristocratic name and title (Count von Bronckhorst and Gronsfeld, Baron of Battenburg and Rimburg, Lord of Alphen and Humpel), he had a long military career, and developed a variation of the Vigenère cipher to protect his military correspondence. It works by using a shift that’s determined by a code. If the code is 321, the letters shift three times, then two times, then one time before it all repeats again. Despite being similar, this cipher is weaker than the Vigenère cipher because it only has 10 cipher alphabets, rather than 26, but it has the advantage that numbers are usually harder to guess than secret keys.
Fun Facts and Historical Info

Since it was first developed in the mid-16th century, the Vigenère cipher has been popular in the cryptography and code-breaking community. Even as it sat unbroken, it inspired many other encryption schemes, and was given the nickname “le chiffre indéchiffrable” (French for “the undecipherable cipher”). Here are some more interesting facts about this 5-century-old cipher.
Despite being called the Vigenère cipher in honor of Blaise de Vigenère, it was actually developed by someone else entirely
Alchemist and diplomat Blaise de Vigenère received the credit for inventing the cipher due to a 19th century misattribution. The 19th century author, in reading de Vigenère’s book Traicté des chiffres ou secrètes manières d'escrires, thought that he was describing a cipher that he himself invented. It’s clear to modern authors and cryptographers that Giovan Battista Bellaso, who was born around the same time as Blaise de Vigenère, is actually the author of the cipher.
Giovan Battista Bellaso was one of the first cryptographers to innovate the use of a secret key to identify the alphabets used in encryption.
Bellaso published a treatise on cryptography called “La Cifra del Sig. Giovan Battista Bellaso” (“The Cipher of Mr. Giovan Battista Bellaso”) in 1553. He went on to publish two more booklets on ciphers and cryptography, complete with a challenge to his rivals to solve the complex cryptograms that he hid within his published work. He even promised to reveal their contents within a year, but this does not appear to have ever happened. To this day, no one has solved the Bellaso ciphers.

Despite not being the true author of this cipher, Blaise de Vigenère had an illustrious career in politics and cryptography.
Born in central France in 1523, Blaise de Vigenère entered the diplomatic service at the age of seventeen. It was on a diplomatic mission to Rome that he first began to study cryptography, after reading books written by Alberti and Trithemius throughout his young adult life. Once he made enough money in the diplomatic service, he retired to a life of study. It was during his retirement that de Vigenère created another cipher, the autokey cipher, which is stronger than the cipher that now bears his name.
The Vigenère cipher was thought to be unbreakable until the early 20th century, despite the fact that mathematician and computing pioneer Charles Babbage broke a variant of it in 1854.
Charles Babbage is most famous for his ‘Difference Engine’, which was a precursor to the modern computer that could perform mathematical calculations. He is thought to have broken a variant of the cipher in 1854, but never formally published his work.
Friedrich Kasiski was the first person to publish a successful attack on the cipher.
German cryptographer Friedrich Kasiski published his work on the Vigenère cipher as part of his 1863 book Die Geheimschriften und die Dechiffrir-Kunst (“Secret Writing and the Art of Deciphering”). His method relied on analyzing the distance between repeated fragments of the cipher text, which can give the code-breaker a hint at the length of the secret key. Unbelievably, after he published his book, Kasiski turned away from cryptography to focus his attention on archaeology. It’s believed that he died without realizing how revolutionary his work was to the field of cryptanalysis.
The Vigenère cipher was just one of a few different ciphers used during the Civil War.
The Confederates relied on the cypher often to encrypt their communications. One captain named Campbell Brown, who served under General Joseph E. Johnston, wrote about the difficulty of the Vigenère cipher in his memoirs, saying: “the system I don’t know the name of — it was on the principle of the ‘asymptotes of the hyperbola.’ It was tedious work to decipher — equally laborious to write in cipher.” Despite the fact that officers like Brown would have been trained to write using these ciphers, mistakes were common. During the siege on Vicksburg, an encrypted message was sent to General Edmund Kirby Smith, begging for reinforcements. However, the text was so badly encrypted that by the time his officers figured out the message, it was too late to send help.

Vigenère ciphers are often used in pop culture and fun cryptographical activities like geocaching and CTFs.
Recently, it’s been mentioned in shows like NCIS: New Orleans, and the Disney Channel kid’s program Gravity Falls. It was also mentioned in the novel “The Spy Who Couldn’t Spell” by Yudhijit Bhattacharjee, and was used by fans to solve a puzzle hidden in the expansion pack of the video game Destiny 2.
Try your code-breaking skills
Code-breaking is not only fun, but also a very good exercise for your brain and cognitive skills. Why don’t you try breaking this puzzle?
dl wzyhk xj gz a gvh nuemwzdc rudl xdfg a kzn og su uiv cjo hmwo uyemo ncaw dm v nims ggrb djmviyt qsp mzw wvcy llz wjoemxgq pdii omob v oldgkwv d bvniin ozi xipjeby og ozyk lvvgkarb zjjiqym omobjmx byolmia vfcrbzji vn vdp
See also: Code-Breaking tools | Adfgvx cipher | Adfgx cipher | Affine cipher | Atbash cipher | Baconian cipher | Beaufort cipher | Bifid cipher | Caesar cipher | Columnar transposition | Cryptogram | Double transposition | Enigma machine | Four-square cipher | Gronsfeld cipher | Keyed caesar cipher | One-time pad | Pigpen cipher | Playfair cipher | Rail fence cipher | Rot13 | Route transposition | Substitution cipher | Trifid cipher | Variant beaufort cipher